Poll Results: Manager is the Most Challenging Role in GRC
The people have spoken and chose the GRC Manager as the most challenging role in Governance, Risk, and Compliance (GRC). Take it from one of our very...
24/7/365 Monitoring & Alerting
Compromise Assessments
Threat Hunting
Vulnerability Management
CMMC Preparation & Assessment
Cybersecurity Assurance Readiness (CSAR®/RMF Pro)
ATO/RMF Support
If you are concerned about a potential threat or are experiencing a breach, contact our 24/7/365 emergency hotline at 888-860-0452.
 Subscribe to NetSec News
Subscribe to NetSec NewsSign up to receive our biweekly newsletter that covers what's happening in cybersecurity including news, trends, and thought leadership.
At our core, Ingalls is a company that strives to be helpful to our clients while continuously innovating and evolving our technology and solutions. Since 2010, we have been dedicated to building a team and product that can stay steps ahead of threats, attacks, and vulnerabilities in an ever-changing landscape.
1 min read
 Brandi Pickett
:
May 18, 2022 12:00:00 AM
Brandi Pickett
:
May 18, 2022 12:00:00 AM
The people have spoken and chose the Threat Hunter as the most challenging role in cybersecurity. Take it from one of our very own Threat Hunters, Sean Scully, who discusses how he manages the challenges of this role.

The people have spoken and chose the GRC Manager as the most challenging role in Governance, Risk, and Compliance (GRC). Take it from one of our very...
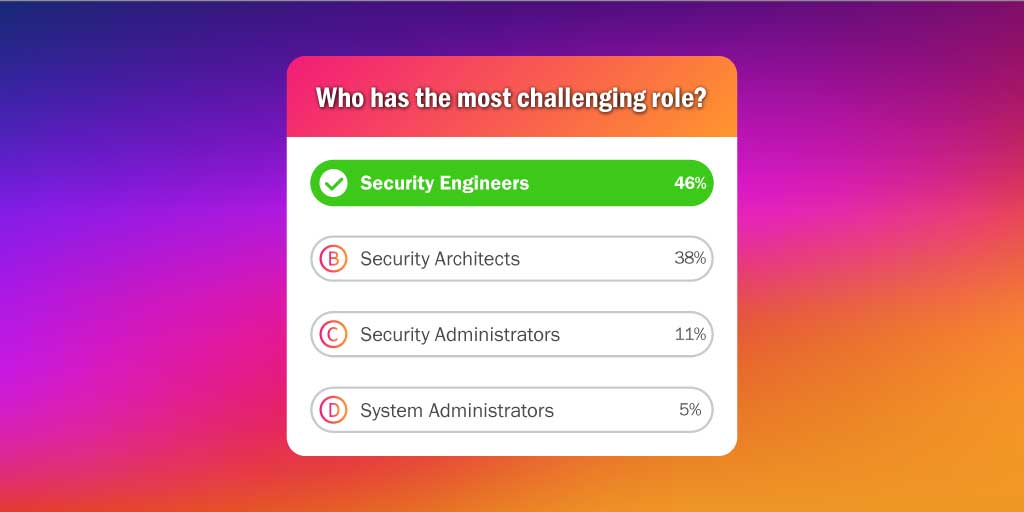
The people have spoken and the poll results show that Security Engineer is the most challenging role in security development and integration....

In this Intern Review, we hear from Cierra Moret about what it's like working at Ingalls and what's next in her cybersecurity career journey.