The Phishing Adventures of Huck Phinn, Casting Wide Nets
Chapter 6 In the previous chapter, all seemed well with Huckleberry “Huck” Phinn and the St. Petersburg Wildlife Foundation. Huck and the gang at St....
24/7/365 Monitoring & Alerting
Compromise Assessments
Threat Hunting
Vulnerability Management
CMMC Preparation & Assessment
Cybersecurity Assurance Readiness (CSAR®/RMF Pro)
ATO/RMF Support
If you are concerned about a potential threat or are experiencing a breach, contact our 24/7/365 emergency hotline at 888-860-0452.
 Subscribe to NetSec News
Subscribe to NetSec NewsSign up to receive our biweekly newsletter that covers what's happening in cybersecurity including news, trends, and thought leadership.
At our core, Ingalls is a company that strives to be helpful to our clients while continuously innovating and evolving our technology and solutions. Since 2010, we have been dedicated to building a team and product that can stay steps ahead of threats, attacks, and vulnerabilities in an ever-changing landscape.
5 min read
 Cyrus Robinson
:
Oct 4, 2022 12:00:00 AM
Cyrus Robinson
:
Oct 4, 2022 12:00:00 AM
It's Cybersecurity Awareness Month, so we thought it was a good time to bring back our good friend Huck Phinn for another adventure in phishing.
It has been a while since poor Huck got tricked by that phishing email from Tom in the previous chapter, and has made sure to be very careful ever since. Things were looking up, and it was the perfect time to go on a little vacation. After his shift at St. Petersburg Wildlife Foundation, Huck got online and scheduled a trip to visit his favorite aunt, Polly. While planning his trip, Huck received an email from Jim, another one of his most trusted pals. Jim is a known attorney at the Pearl Law Firm in Missouri, and he has a lot of contacts throughout the state of Missouri. Since Jim is a close pal, Huck quickly opened the email from Jim. It said “Please find your invoice attached” and had an Excel document attachment.
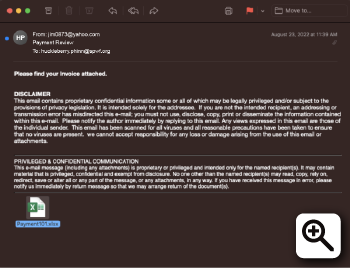 Figure 1 - The original phishing email that Huck received from Jim
Figure 1 - The original phishing email that Huck received from Jim
Just when Huck was about to click on the attached Excel document, he took pause. This seemed strange and oddly like a phishing email hoping to steal his precious information. He took a moment to think and decided to call his assigned Primary Analyst within the Ingalls SOC who encouraged him to forward this email to his Ingalls Information Security Phishing Email Helpdesk for analysis.
Figure 2 - VirusTotal results for the Excel document attachment
The email did not contain any malicious macros or exploits. It only contained an image claiming to be a “Citrix Attachment” and a button named “Click Here to View Documents” linking to www.evernote[.]com/shard/s516/sh/953c2874-f4b0-1e6f-eb9a-beb7fed2bfc5/4ffdc5a82661e539 6f311f4e6fe42e82.
Figure 3 - Malicious benign Excel document with a button leading to Evernote page.
By sending the email from a trusted colleague’s legitimate, although compromised, email address, the threat actor avoided suspicion of some recipients and their email security systems, and the threat actor also evaded quarantine of the attachment because the attachment itself did not contain any malware. Finally, the threat actor managed to prevent the network traffic from the link being considered malicious by linking to an Evernote page. Evernote is a great vehicle for malicious delivery of payloads because it is a very popular mobile device and web notekeeping application that is unlikely to arouse suspicion or result in alerts in network logs and is unlikely to be blocked by security teams. The Ingalls Phishing Helpdesk clicked the link.
Figure 4 - Evernote page linked to from the Payment101.xlsx Excel document
The Evernote page has a subject stating “Payment Review” with an image of the Excel logo and the text “View Invoice”, which contains a link to another website with the actual “payload” of this phishing campaign. At the time that Huck submitted the email to the Ingalls SOC, this link went to a compromised WordPress website at uncommonroadmusic[.]com/otzozukadzima/index.html.
Figure 5 - “Microsoft” credential harvesting page linked to from the Evernote page
When the analyst clicked on the “View” button, the Ingalls Phishing Helpdesk was taken to the credential harvesting form designed to look like a Microsoft login.
Figure 6 - Credential harvesting form on the compromised uncommonroadmusic[.]com website
It is not hosted at a valid Microsoft domain. The login form is not the actual form presented to user’s logging into a Microsoft domain. The payment101.xlsx file says that the invoice document name is EFT Number 202206063377997.pdf, but this document is apparently named “INV-40211.pdf” instead. A legitimate invoice is unlikely to be delivered by being delivered via Microsoft One Drive.
The Ingalls Phishing Helpdesk entered fake credentials into the form and clicked on the “View” button to submit the form:
The fake credentials that the analyst entered, could be seen being delivered, in plain text, to the threat actor via another page on the compromised domain.
Figure 7 - Harvested credentials delivered to the threat actor
The Ingalls Phishing Helpdesk then used Endpoint Detection and Response (EDR) tools to check if the Excel document or traffic to the uncommonroadmusic[.]com domain was seen in other client environments, and it was seen in at least five other Ingalls’ client environments throughout Missouri: Hospital of Cottlevalley Association, St. Charles Center, Missouri Decatur College, Springfield Clerks Association, and St. Louis Law firm. Unfortunately, a couple of these clients had accounts compromised and the email had been sent to all their email contacts.
During the investigation, Ingalls SOC noticed that while the Evernote page was seen linking to a compromised uncommonroadmusic[.]com address, it originally linked to majesticmasonry[.]org. However, it appears that once the majesticmasonry[.]com domain became marked by Google Chrome and security tools as malicious, they switched to uncommonroadmusic[.]com. Having the credential harvesting site hosted on multiple compromised domains, allowed the threat actors to quickly change the payload linked on the Evernote page in order to avoid being blocked and losing potential phishing victims.
In order for this campaign to work, the victim needed to 1) open the phishing email, 2) download and open the Excell document, 3) click on the link to Evernote in the Excel document, 4) click on the “View Invoice” link in the Evernote document, 5) click “View” on the credential harvesting page, 6) enter their credentials into the fake login form, and 7) not have MFA enabled for their email account. Having so many steps involved might make a user less likely to follow through to the end and to have their credentials harvested, but they also provide layers of abstraction that allow the threat actors to avoid detection, ensuring the long-term success of their campaign.
As an additional precaution, Ingalls globally quarantined the filehash of the Excel document and blocked the IP addresses and domains of the credential harvesting pages within their Client environments. The Ingalls SOC also notified Clients who were known to have received or downloaded the document about the campaign and provided them with recommendations to keep their environments safe. Finally, the Ingalls SOC also reached out to the system administrator of Jim’s organization to inform them about the phishing campaign.
Would you have spotted all of the red flags? Do you know someone who might have taken the bait? Download and share our “How to Spot a Phish” checklist to elevate security awareness and keep more people safe online.
|
Our “How to Spot a Phish” checklist can help you identify phishing emails and provides advice on what to do with them. |

|

Chapter 6 In the previous chapter, all seemed well with Huckleberry “Huck” Phinn and the St. Petersburg Wildlife Foundation. Huck and the gang at St....

Chapter 3 In the previous chapter, Huck Phinn, who works for an environmental group, narrowly escaped a phishing email trap by recognizing red flags....

Chapter 2 In Chapter One we mentioned that the most common phishing attacks are mass emails sent to as many recipients as possible in hopes that even...