What You Need to Know About CISA's New Cybersecurity Strategic Plan
The Cybersecurity and Infrastructure Security Agency just released its FY2024-2026 Cybersecurity Strategic Plan. This new Strategic Plan was written...
24/7/365 Monitoring & Alerting
Compromise Assessments
Threat Hunting
Vulnerability Management
CMMC Preparation & Assessment
Cybersecurity Assurance Readiness (CSAR®/RMF Pro)
ATO/RMF Support
If you are concerned about a potential threat or are experiencing a breach, contact our 24/7/365 emergency hotline at 888-860-0452.
 Subscribe to NetSec News
Subscribe to NetSec NewsSign up to receive our biweekly newsletter that covers what's happening in cybersecurity including news, trends, and thought leadership.
At our core, Ingalls is a company that strives to be helpful to our clients while continuously innovating and evolving our technology and solutions. Since 2010, we have been dedicated to building a team and product that can stay steps ahead of threats, attacks, and vulnerabilities in an ever-changing landscape.
4 min read
 Kim Buckley
:
Aug 9, 2023 12:00:00 AM
Kim Buckley
:
Aug 9, 2023 12:00:00 AM
In today's ever-changing digital world, ensuring the security of your valuable data and maintaining customer trust is of utmost importance for businesses and organizations. Recognizing the need to enhance cybersecurity practices in all sectors, the Cybersecurity and Infrastructure Security Agency (CISA) is committed to this mission. As a cybersecurity consultant, our goal is to assist organizations in not only meeting but surpassing the CISA Cybersecurity Performance Goals (CPGs). In this blog, we will outline the crucial objectives set by CISA and demonstrate how Ingalls’ Consulting Services can empower your organization to achieve excellence in cybersecurity.
CISA's Cybersecurity Performance Goals (CPGs) are a subset of cybersecurity practices, selected through a thorough process of industry, government, and expert consultation, aimed at meaningfully reducing risks to both critical infrastructure operations and the American people. These voluntary CPGs strive to help small- and medium-sized organizations kickstart their cybersecurity efforts by prioritizing investment in a limited number of essential actions with high-impact security outcomes.
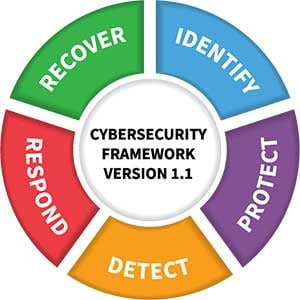 The CISA CPGs are organized, ordered, and numbered to align closely with the National Institute for Standards and Technology (NIST) Cybersecurity Framework (CSF): Identity, Protect, Detect, Respond, and Recover to help organizations more easily use the CPGs to prioritize investments as part of a broader cybersecurity program built around the CSF. The NIST CSF is a widely recognized and widely used framework that provides a flexible, risk-based approach to managing and improving an organization’s cybersecurity posture. Let’s explore how the CISA CPG aligns with the NIST CSF.
The CISA CPGs are organized, ordered, and numbered to align closely with the National Institute for Standards and Technology (NIST) Cybersecurity Framework (CSF): Identity, Protect, Detect, Respond, and Recover to help organizations more easily use the CPGs to prioritize investments as part of a broader cybersecurity program built around the CSF. The NIST CSF is a widely recognized and widely used framework that provides a flexible, risk-based approach to managing and improving an organization’s cybersecurity posture. Let’s explore how the CISA CPG aligns with the NIST CSF.
CISA's first goal revolves around identifying and protecting the organization's critical assets.
CISA CPG Goal 1: Protecting Critical Assets
CISA CPG Goal 2: Defending Against Cyber Threats
The first two CISA CPG goals align with the NIST CSF "Identify" function. This involves understanding and managing cybersecurity risks to systems, assets, data, and capabilities. Goal 1 focuses on identifying critical assets, such as sensitive data and infrastructure, while Goal 2 emphasizes the need to defend against cyber threats, indicating a proactive approach to identifying potential risks.
The second goal is to strengthen your organization's ability to defend against cyber threats and attacks.
CISA CPG Goal 1: Protecting Critical Assets
CISA CPG Goal 2: Defending Against Cyber Threats
CISA CPG Goal 3: Securing High-Value Transactions
The protection-oriented CISA CPG goals correspond to the NIST CSF "Protect" function. Goal 1 and Goal 2 encompass protecting critical assets and defending against threats, while Goal 3 focuses on securing high-value transactions. This aligns with the NIST CSF's emphasis on implementing safeguards to limit or contain the impact of cybersecurity events.
CISA CPG Goal 4: Strengthening the Cyber Ecosystem
CISA CPG Goal 5: Improving Situational Awareness
CISA CPG Goals 4 and 5 align with the NIST CSF "Detect" function. These goals emphasize the importance of increasing awareness of cyber threats and vulnerabilities within the organization and the broader cyber ecosystem. By aligning with this core function, organizations can identify and respond promptly to potential cybersecurity incidents.
A secure cyber ecosystem is not just about individual organizations protecting themselves but also about collaborating with stakeholders to enhance the overall resilience of the digital landscape.
CISA CPG Goal 2: Defending Against Cyber Threats
CISA CPG Goal 4: Strengthening the Cyber Ecosystem
CISA CPG Goals 2 and 4 are related to the NIST CSF "Respond" function. They emphasize the need to develop and implement an effective incident response plan, allowing organizations to respond rapidly and effectively to cybersecurity incidents and reduce their impact.
CISA CPG Goal 2: Defending Against Cyber Threats
CISA CPG Goal 4: Strengthening the Cyber Ecosystem
CISA CPG Goals 2 and 4 also align with the NIST CSF "Recover" function. These goals stress the importance of recovery planning and improving organizational resilience to recover quickly from cybersecurity incidents.
By structuring the CISA CPGs to align with the NIST CSF, organizations can seamlessly integrate their cybersecurity efforts and leverage the NIST framework's established best practices and guidelines. This alignment ensures a comprehensive and coherent approach to cybersecurity management, enabling organizations to strengthen their defenses, improve incident response, and enhance overall cybersecurity readiness.
Complying with the CISA CPGs not only enhances an organization's overall cybersecurity posture but also plays a crucial role in supporting federal grant requirements. Federal grant requirements often include provisions related to cybersecurity, and adherence to the CISA CPG can help organizations meet these requirements in the following ways.
Federal grant providers expect recipients to exercise due diligence in managing and securing their funds and resources. Complying with the CISA CPG showcases a proactive approach to cybersecurity, indicating that your organization takes data protection and risk mitigation seriously. This can positively impact your eligibility for federal grants, as it reflects responsible stewardship of government funds.
Many federal grants come with specific cybersecurity requirements and regulations that organizations must meet. These regulations often align with industry standards and best practices, including the CISA CPG. By adopting CISA's performance goals, your organization can demonstrate compliance with these regulations, which is essential for grant eligibility and continued funding.
If your organization is using federal grant funds for specific projects or initiatives, ensuring the security of those projects is critical. Cyberattacks or data breaches can not only disrupt the progress of these projects but also jeopardize sensitive information related to them. Complying with the CISA CPG helps protect the integrity and confidentiality of grant-funded projects, reducing the risk of costly disruptions.
Federal grant providers need to have confidence in the organizations they fund. By adhering to the CISA CPG, your organization demonstrates a commitment to safeguarding data, systems, and resources, thus fostering trust and accountability. This can positively influence federal grant providers' decisions to award or renew grants to your organization in the future.
In the event of a data breach or cybersecurity incident, organizations may face legal and financial liabilities. Complying with the CISA CPG can help reduce the likelihood of such incidents occurring, minimizing potential legal repercussions and associated costs. Grant providers may view organizations that actively work to mitigate cybersecurity risks as lower-risk recipients.
Some federal grants involve handling sensitive information, such as personally identifiable information (PII), financial data, or research findings. Cybersecurity breaches involving this data can lead to severe consequences. Adhering to the CISA CPG helps ensure that appropriate security measures are in place to protect such sensitive information from unauthorized access or disclosure.
In summary, complying with the CISA CPG provides a comprehensive and structured approach to cybersecurity, which can align with federal grant requirements and expectations. Demonstrating a commitment to strong cybersecurity practices not only supports federal grant compliance but also enhances an organization's reputation, trustworthiness, and long-term viability as a grant recipient.
As a cybersecurity consultant, we are committed to helping your organization achieve excellence in cybersecurity and compliance with CISA's CPG. By partnering with us, you gain access to a team of skilled consultants dedicated to securing your critical assets, defending against cyber threats, and strengthening your cybersecurity posture.
Ingalls Professional Services capabilities and expertise include:
Contact our Consulting Team today to learn more.

The Cybersecurity and Infrastructure Security Agency just released its FY2024-2026 Cybersecurity Strategic Plan. This new Strategic Plan was written...

Ingalls has consolidated relevant and helpful information to address security and privacy concerns surrounding the global COVID-19 outbreak. This...

1 min read
In September 2021, multiple security research teams observed and reported email reply-chain attacks that distributed new SquirrelWaffle Loader and...